Tracy Pitcher, Senior Vice President of Comcast Business, Central Division
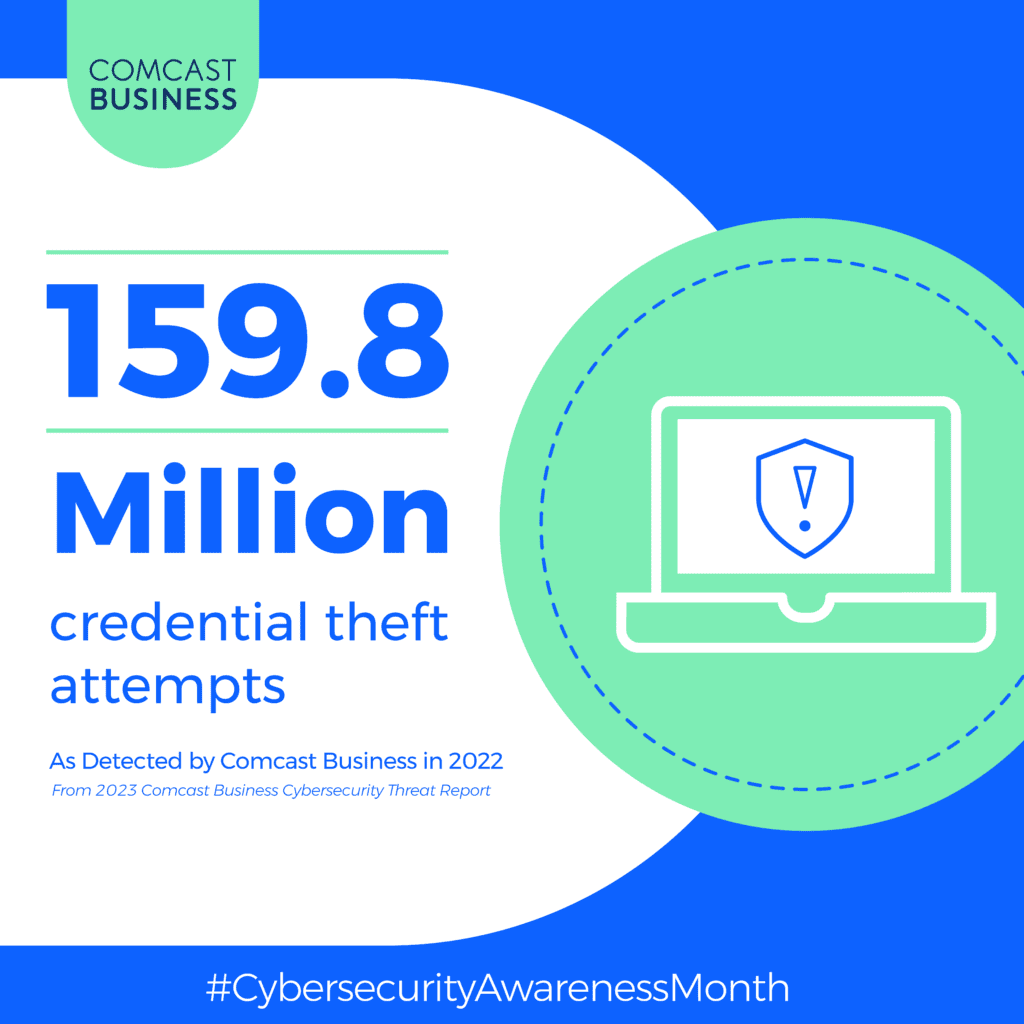
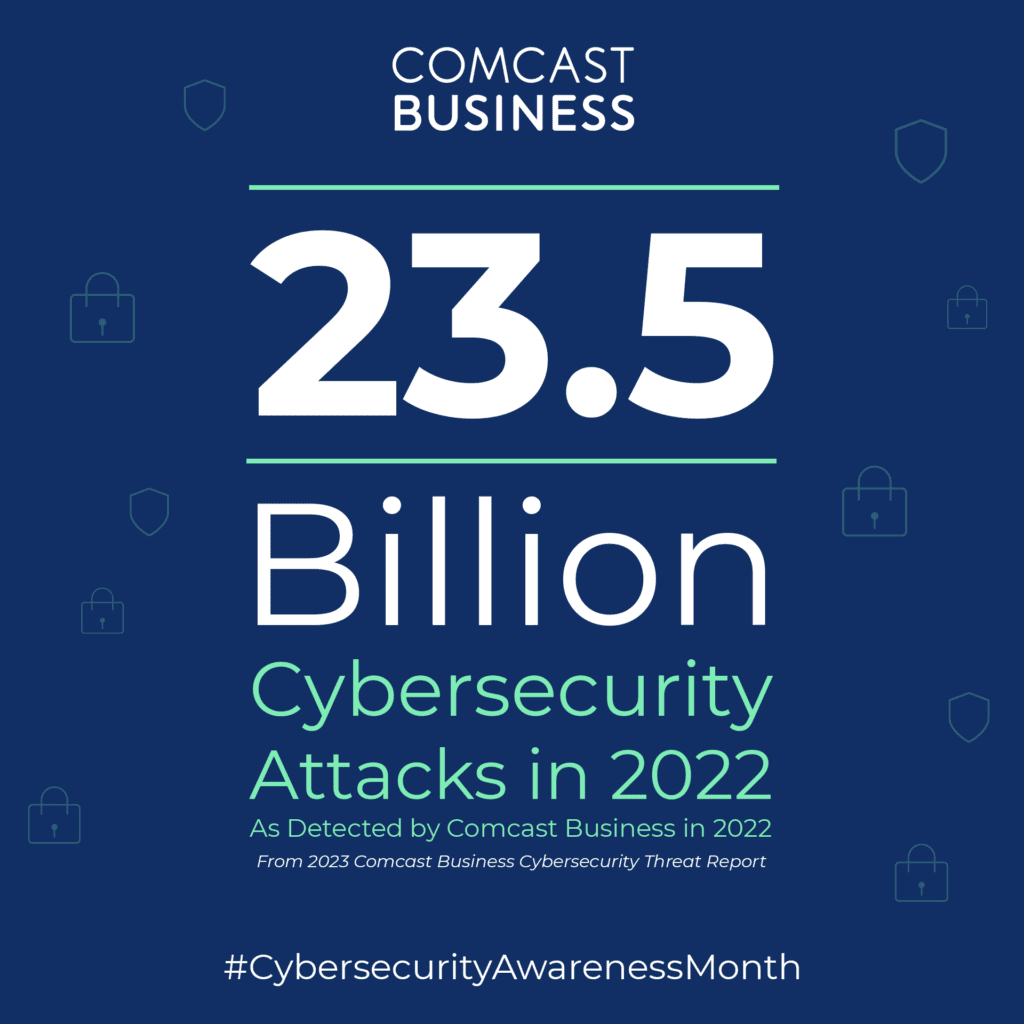
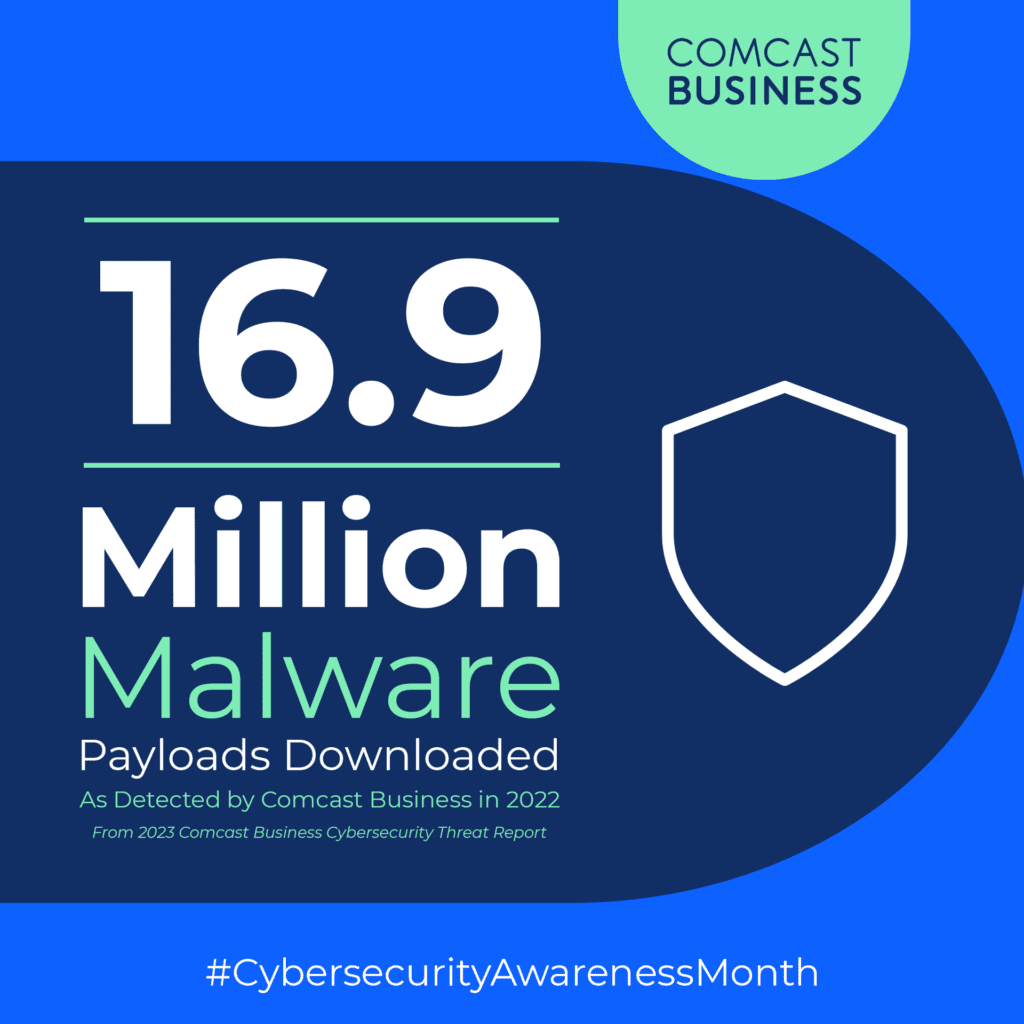
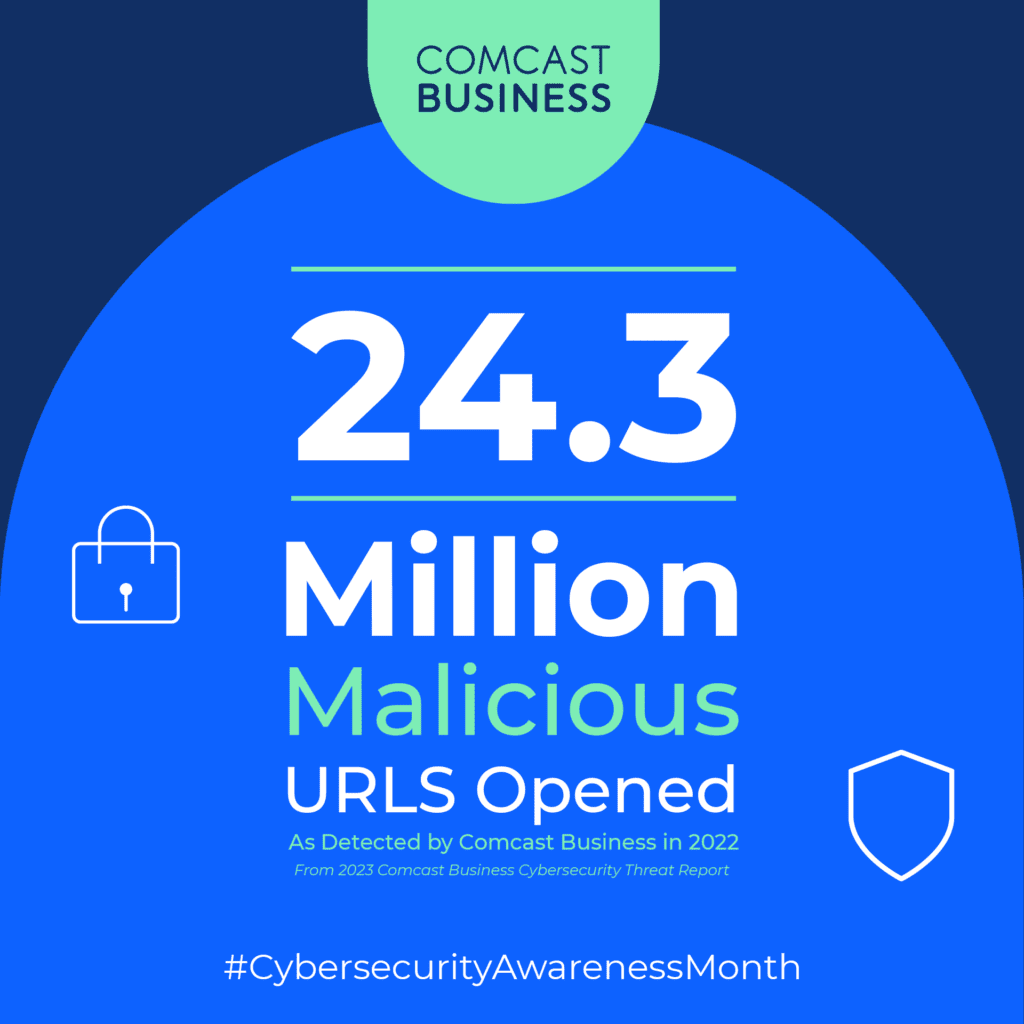
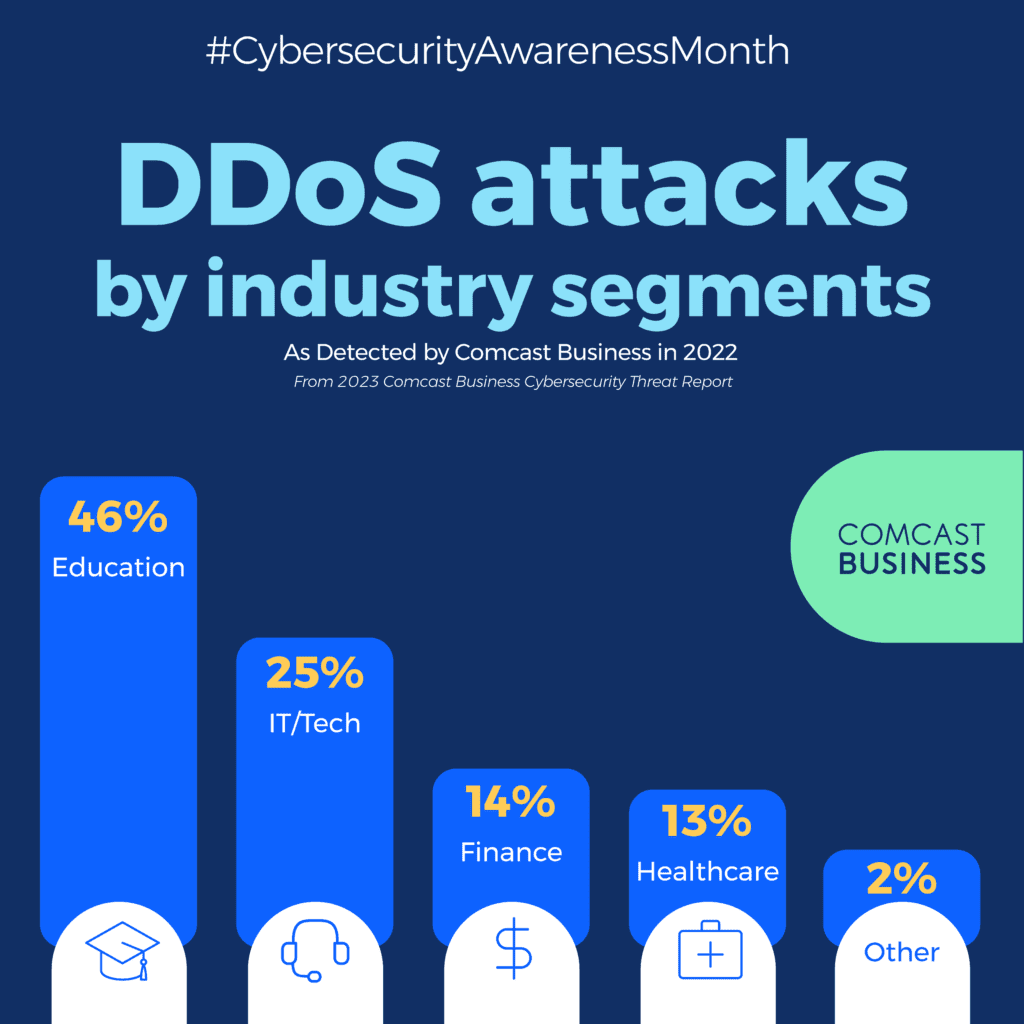
Robust cybersecurity measures are essential for enterprise organizations. These businesses often find themselves targets of cyberattacks thanks to the large amounts of sensitive – and therefore valuable – data they have. Despite having access to IT resources to mitigate threats, the cyberthreat landscape continues to evolve in the scale, complexity and sophistication of its attacks. In fact, the 2023 Comcast Business Cybersecurity Threat Report found that of the 24 billion attempted cybersecurity attacks in 2022, there were 500 unique threat types and 900 distinct infrastructure and software vulnerabilities.
In today’s interconnected world, the disruption caused by cyber threats can cripple operations, affecting productivity and compromising the integrity of systems and data. A breach can also result in substantial financial losses, legal repercussions, and damage to the organization’s reputation. Indiana’s enterprise organizations play a key role in ensuring both the health of the state’s economy and the success of its workforce, so they cannot afford network downtime or loss of access to their networks.

To help protect against the latest threats in the cyber landscape, here are four key considerations from Comcast Business for enterprise organizations to keep in mind this Cybersecurity Awareness Month:
The rise of a distributed workforce requires foundational shifts in cybersecurity strategies.
An increasingly distributed workforce has resulted in rising adoption of the cloud, infrastructure-as-a-service, software-as-a-service (SaaS) applications and the Internet of Things – meaning enterprises must put even more emphasis on a holistic approach to securing their networks. With hybrid work alongside distributed application architectures, it is critical to protect all traffic flows as users, corporate data and business-critical assets are now more likely to reside anywhere and increase an enterprise’s exposure to security risks.
As organizations look to optimize their security measures, they are shifting toward software-defined wide area networking (SD-WAN), micro-segmentation and threat response automation technologies. These solutions can streamline network threat monitoring and management, help businesses secure their corporate data, as well as manage the attack surface through network segmentation.
Knowing an organization’s complete network footprint helps mitigate attacks.
If an enterprise organization is going to rethink its approach to cybersecurity solutions, first it must understand the full scope of its network and the potential points of risk. Organizations should have a clear view of all their assets, corporate data, personally identifiable information applications and systems whether on the network, in the cloud or on a home user device.

When it comes to the cloud in particular, the use of cloud resources is very convenient, but oftentimes when a campaign is over, organizations forget to disable the application – which means it’s still available and could be an outlet to threat. It’s important that organizations are aware of their cloud footprint to ensure unused applications are removed. This added level of scrutiny and validation ensures businesses and customers aren’t vulnerable to leaky, unused cloud apps that could cause a potential customer data breach.
New technologies offer workflow efficiencies, but also create new potential for cyberattacks.
With the release of ChatGPT in November of 2022, generative AI — a branch of artificial intelligence that creates new text, images, video and other content — went mainstream. While enterprise organizations have been exploring how it might support their operations, Generative AI’s newfound position in the spotlight also brought with it discussions of how to prevent malicious and inappropriate applications, dangers that become increasingly apparent when viewed through the lens of cybersecurity.
Not only can generative AI tools be used to take social engineering to new levels by creating more sophisticated attacks with more convincing text, images, video, and voice to target victims, but they also lower the barriers to entry for cybercriminals. Previously, hackers needed some combination of coding, writing, and/or graphic design skills to launch a convincing attack. Now almost anyone with the desire and access to the internet can do so.
To counter this, enterprise companies should start by thoroughly reviewing their security postures, including assessing current systems, identifying vulnerabilities and making the necessary adjustments to increase protection. AI security and automation tools can strengthen network defenses and help level the playing field by distinguishing real threats from false alarms, thereby freeing security staff to focus only where they are needed most.
Partnering with a third party helps fill gaps in an enterprise’s cybersecurity team.
The challenge of keeping up with the rapid pace of change in cybersecurity threats can be daunting, even for the most experienced IT teams. This is where a managed security service provider (MSSP), like Comcast Business, can help by bringing extensive expertise, resources, and up-to-date knowledge to the table. By partnering with an MSSP, organizations can effectively offload some of the burden of monitoring and responding to threats, allowing them to focus on their core business functions.

Comcast Business helps its enterprise customers better protect their networks and data via secure architectures leveraging solutions such as SD-WAN, DDoS mitigation and other services in its extensive managed security portfolio. Visit https://business.comcast.com/ to learn more, and to better arm yourself with cybersecurity real-life data, please read 2023 Comcast Business Cybersecurity Threat Report and the 2023 Comcast Business Small Business Cybersecurity Report.